Defense
Cyber Security
- 현재 페이지경로
Cyber Warfare Management System
How to secure and maintain the dominance in the cyber battlefield is of the crucial importance for the future warfare. In order to strengthen the ROK Forces’ capabilities to wage cyberwarfare, the fifth war theatre inclusive of land, sea, air and space war theatres, MND has been developing the core technologies with the roadmap to complete Cyber Warfare Management System by the year 2023.
Cyber Warfare Management System is comprised of three main areas: cyber intelligence gathering, cyber command and control and cyber active response. By fully leveraging its weapon system development capabilities for ground, sea, air and space platforms, Hanwha Systems is leading the R&D efforts to develop Cyber Warfare Management System as well as other weapon systems’ cyber security technologies thru cyber warfare related core technology R&D projects and product developments.
- Features
-
-
Cyber ISR(Intelligence, Surveillance &
Reconnaissance) Collection,
Compilation and Analysis of Cyber
Assets and Threat Information
Concerning Friendly Forces and Foes -
Cyber C2(Command and Control)
Cyber Operation Command and
Control Based on Battlefield Situation
Information Analysis and Intuitive
Visualization -
Cyber Active Response Including
Cyber Threat Intrusion Tolerance thru
Enemy Forces’ Cyber Assault Detection,
Analysis and Inference
-
Cyber ISR(Intelligence, Surveillance &
Core Technologies
-

- Cyber ISR
-
- Information management for cyber assets and weak points
- Threat intelligence information analysis
- Association analysis of physical warfare threat information and information fusion
- Cyber threat information distribution and sharing
-
- Cyber C2
-
- Battlefield situation information fusion
- Assessment of impact on the mission or damages
- Management of cyber operation elements and assessment of their effectiveness C
- Cyber COP(Concept of Operations)
-

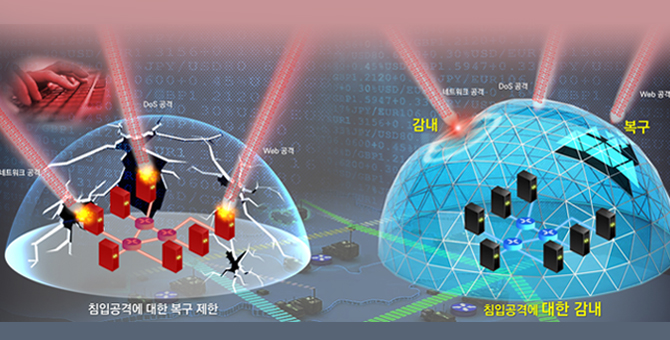
- Cyber Active Response
-
- System/Network intrusion tolerance
- Decoy system to entice intrusion
- Analysis of enemy’s assault pathways and origin points
- Detection of insider threats